Social Networking Systems: History, Critique, and Knowledge Management Potentials
A multiplicity of social networking services (SNS) have been introduced within the last several years. SNS Web sites such as Friendster have rapidly gained subscribers who seek to augment their personal social network, to seek new relationships, or to access various, peer-created or collected information. These recent SNS Web sites differ from their less formal predecessors, such as UseNet newsgroups, in that they make direct relational links and allow representations beyond purely text. Social networking is innate to the human cultural experience, but the concept is not new to electronic networks – bulletin boards and other forums have served the same purpose. These applications are popular because they focus on personal relationships and orient on specific social or informational goals. SNS sites attract participants with interests ranging from making business contacts to dating and leisure activities. Likewise, SNS sites facilitate narrowly focused information exchange including recommendations, news, editorial and personal narrative, and so on. Each of the current SNS applications appeals to a basic human desire for connection and inclusiveness within a social group or activity.
By modeling real social networks in a virtual environment, SNS adds value to the existing networks by multiplying the potential for connection and by centralizing communications between its members. Unfortunately, the increasing choice of SNS sites, lack of data portability between applications, simplistic relationship models, and inability to control facets of personal data threatens to prevent the technology from maturing. Additionally, market failure for SNS technologies would detract from the potential these applications have for improving personal and organizational knowledge management applications.
Electronically Augmented Social Networks
As new electronic communications protocols and applications have been introduced, social networks have eventually formed around them. When the technologies become more engaging and participative, the social networks around them become more complex. For instance, telephony allows people to augment their social relationships with others by providing direct, synchronous communications. The telephone as an extension of social networks was unforeseen at the time of its introduction, and, as with newer technologies, it was often seen as detracting from the social experience (Poster, 2001, p. 81; Lasen, 2002, p. 20-21). Nevertheless, the telephone as a communications device has had definite effects on people's social behavior.
Computer-mediated communication networks were developed in the 1960s which included ARPANET, the predecessor to the Internet (Wellman, et al., 1996, p. 213). The users of the nascent Internet formed into small, tightly-bounded groups (to use Wellman's (1996) terminology) of specially trained users, for which any social network analysis would have been less than compelling – everybody involved likely had connections to most everyone else. For example, early Unix programmers, enabled by the Internet and united by a common interest in developing code for the emerging operating system, formed some of the earliest online communities (Rheingold, 2002, p. 50). These early examples show that wherever people communicate about common interests or problems they are likely to form relationships, with the strength and range of relationships being bound by the affordances of the technology and the size and diversity of its user population.
Some of the earliest, well-populated, electronic social networks emerged in the 1970s (Wellman, et al., 1996, p. 213). E-mail lists and bulletin board systems (BBS) were some of the first technologies to facilitate mass social collaboration and interaction online. Interactions on e -mail lists and BBSs are textual and asynchronous, yet allow for the development of stable and long lasting relations between, often pseudonymous, individuals (Smith, 1992, p. 6). UseNet and Internet relay chat (IRC) extend the messaging concept by enabling relatively unrestricted participation in groups with similar interests or defined characteristics. UseNet, created in 1979, shares messages among an open, ad-hoc network of news servers and organizes them in collections called “newsgroups.” UseNet was estimated in 2000 to have over 8.1 million unique users, making it not only one of the earliest online communities, but perhaps the largest (Rheingold, 2002, p. 53-54). In contrast to the persistent, asynchronous communication of UseNet, IRC connects users through synchronous chat communications in virtual spaces called “channels” that are informally organized by specific social groups or about specific subjects. UseNet and IRC as forums are not exclusive and have low barriers to entry – all one need have is a connection to the network and some basic software. Despite their inclusiveness, or perhaps because of it, UseNet and IRC facilitate the formation of personal relationships and group identities through pseudonymous discussions about particular interests with varying degrees of informality (Reid, 1996; Kling, 1996).
Instant messaging (IM) applications such as AOL Instant Messenger and ICQ first appeared in 1996. These applications create a near-synchronous messaging environment that merges aspects of real-time chat and e-mail (Huang & Yen, 2003, p. 64; Nardi, et al., 2000, p. 2). In contrast with e-mail lists or BBSs, which restrict membership based on a global list, IM applications maintain relationships in ad-hoc networks as defined by the user. IM clients maintain lists of people with which the user has some relations or desire to communicate, and uses a negotiation model for adding new contacts to one's list or restricting the addition of one's account to another's list. In addition to messaging, IM clients often integrate content features, such as file transfer and email, as well as synchronous communication via multi-party chat (Huang & Yen, 2003, p. 65). Because of these content and relationship management features, IM provides the prototypical configuration for current SNS technology. Similarly, IM clients are used for a range of social and work purposes which further strengthens the parallels between IM and current SNS applications (Huang & Yen, 2003, p. 64).
Online games provide another method for groups to form and associate. Multi-user domains (MUDs) are textual gaming environments which are the predecessors to today's online, multi-player games. MUDs, unlike e-mail or online discussion groups, construct a continuous, real-time, virtual environment by employing physical and spatial representations (Mnookin, 1996, p. 246). Interactions with other users within the MUDs are essentially anonymous which encourages experimentation with identity, community, and personal or group relationships. Since these online environments simulate real environments, the behavior of its users tend to replicate aspects of real social interactions, replete with hierarchies, customs, rules, and even legal systems (Mnookin, 1996). These early social networking technologies formed loose bonds between people, or, more accurately, between people's representations of themselves online. These bonds, however, are not enforced by the system's architecture or otherwise referentially enforced in any way, with the possible exception of forced expulsion. Instead, the only records of past interactions exists in archives and log files, and the only record of relationships exists in the individual memories of the users.
The early social networking platforms just described operate primarily on the exchange of textual data. Despite such a high degree of mediation between users, “users of these systems have come to feel that they participate in a community that fulfills many of the roles more commonly found in traditional face-to-face communities” (Smith, 1992, p. 7). Newsgroups, IRC, MUDs, and other real-time or asynchronous communications can provide meaningful social connections, but only at relatively low user populations. With increasing users comes an increase in data transfer and decreasing viability for useful participation in a manner very similar to classical population dynamics. The open and relatively unrestricted nature of many of these media, as well as the sparse, text-only information exchange limited their effectiveness in augmenting real social networks.
Social Networks Meet the Web
By the end of the 1990s, three conditions converged to facilitate the creation of large-scale, unbounded, online social networking applications:
-
The inability of text-based social systems (email, IRC, MUDs) to accommodate tightly-knit, unbounded user populations and rich data representations.
-
A sufficiently large and diverse user population made possible by the popular adoption of the Web (Wellman, et al., 1996, p. 214).
-
Sufficient maturity in systems architecture to be able to accommodate the computational and memory overhead of more complex, distributed applications and that can support large-scale exchanges of representations other than purely text.
The popularity of SNS Web sites has increased rapidly, as has the number of different sites that are available. The most popular SNS sites show membership in the hundreds of thousands, as measured by the number of users within the greater network (Friendster, 2004; Ryze, 2004). Unofficial counts of SNS sites numbered well over 100 by the beginning of 2004 (Meskill, 2004), prompting Cory Doctorow to coin the semi-derisive phrase, “Yet Another Social Networking Site,” (YASNS) in response to the frequency of SNS site introductions (Kahney, 2004). With well over 100 different SNS sites available to the public, an exhaustive review and comparison is not warranted. Rather, the following is an assessment of some of the first and most popular SNS sites and some of their essential features.
The first highly-publicized SNS site, SixDegrees.com, was launched in May 1997. The site's name is based on the phrase, “six degrees of separation,” which was popularized by Stanley Milgram's “small world” experiment (Hayes, 2000, p. 11). SixDegrees provided tools to its users to help them find resources and skills within the network they are connected to, as well as secondary functions such as contact management (Internet Archive, 2004). The site closed down at the end of 2000 due to the market downturn of that year (Liu, 2000).
Ryze debuted in 2001 and extended the SixDegrees idea by applying the social network model to making business and professional contacts (Ryze, 2004). Ryze was initially positioned as a way for high-tech workers to meet at social events with the expectation of building lasting business relationships. Ryze has since expanded to accommodate all types of professional networking activities. The account creation process is simple, but somewhat involved, asking for information regarding employment and resources that the user has to offer the network or is looking to find. In addition to a personal network of friends, the user may join communities, appropriately called “networks,” that resemble e-mail lists or newsgroups and whose content is restricted to registered users. There is also an events listing that encourages face-to-face interaction among users in both Ryze-sponsored and public events. Ryze is free to join, but also offers a “Gold” membership that allows greater access to information and features for a monthly fee.
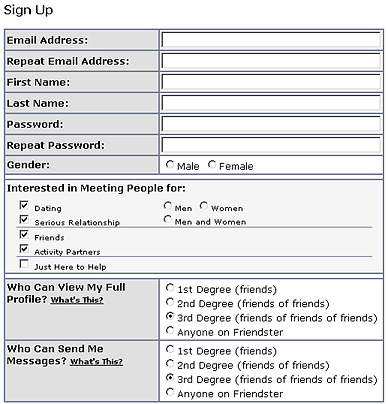
Figure 1: Friendster sign-up form.
In 2003, Johnathan Abrams, an early user of Ryze, introduced Friendster, which was initially designed as a dating and social introduction service (Menn, 2003; Friendster, 2004). New users to the site are asked to complete a short questionnaire that requests demographic data (name, e-mail address, gender) and other data regarding privacy of information and who the user is interested in meeting (see Figure 1). Once an account is created, the user may add details about his or her recreational interests, more detailed demographics, photos, and self-narrative descriptions. The user may then contact other people to join Friendster via a Web form that sends an invitation that will automatically link the new accounts to the originating user. A user may search for existing users by email address or first and last name, somewhat restricting interaction to those who the user already knows. Other users are linked to the account if they request to be linked or if the user asks to be linked, and the request is approved (see also Figure 3).
Another popular, Friendster-like SNS site is Tribe.net (Tribe.net, 2004). Tribe.net has many features in common with Friendster and Ryze: event listings, messaging, personal testimonials, classifieds, user searches, and so on. One of the major differences is a group membership feature named, appropriately, “tribes.” Tribes are groups that users may join, organized in categories much like UseNet newsgroups, that aggregate listings, events, and a discussion board (see Figure 2). A user of Tribe.net may belong to any number of tribes and may freely join public tribes or request to join private ones. Another difference about Tribe.net is that it collects personal and professional information separately. Theoretically, this would allow a user to define who could view the information depending on specified access criteria, but it appears that this separation is only presentational in nature.
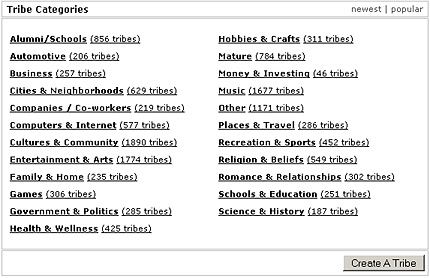
Figure 2: "Tribes" in Tribes.net.
Friendster and Tribe.net were the first of a number of recreational SNS sites to appear in 2003. In addition to business networking and friendship, separate sites exist centering on a myriad of topics such as hobbies (e.g.: Buzznet, Flickr), specific events (e.g.: Six Degree Burn), meeting facilitation (e.g.: MeetUp), pet networking (e.g.: Dogster), information sharing and analysis (e.g.: Eurekster!, RepCheck, StumbleUpon), and item lending (e.g.: MediaVault).
Several features tend to be common to most SNS sites in addition to the basic registration and invitation process. Most sites allow anyone to join, but all have some mechanism to restrict the links that are made with existing users. Additionally, some sites (e.g.: Orkut, LiveJournal) restrict membership to people who are invited by existing members (although LiveJournal will allow paid memberships without requiring an invitation). Users may browse through their personal network of linked users, or search for users within their greater social network by any combination of the user-defined demographic and interest criteria. Several sites facilitate communication using an internal messaging interface. These interfaces allow for anonymous communication within the identity framework of the site, which is important for allowing negotiations between unknown but potential relations. Most sites also have contact management features that extend from the demographic data provided by users. Finally, SNS sites are increasingly focused on providing various types of content presented to users within the social network framework, including personal journals, ratings, and the presentation of documents such as graphics or photos.
Critique of Current SNS Sites
SNS sites are still evolving and maturing. As a result, there are a number of critical points to be made about their current state of implementation:
-
Each site is discrete and proprietary, offering too much choice between sites and diminishing returns for users who join multiple sites.
-
Current SNS sites offer tools that are often already available on the client side.
-
The relationship model employed by SNS sites is overly simplistic.
-
One cannot manage multiple facets of one's online identity without resorting to multiple accounts or, alternatively, collapsing into a single, median identity.
The most obvious problem with the current generation of SNS sites is the number of separate choices. At the time of this writing, there are well over 25 sites with purposes similar to Friendster (Meskill, 2004), each of which has a separate and proprietary user interface. The problem presented to new users of SNS is to choose which site to join. People will most likely choose the site that most of their friends participate in, but those unfortunate people who have a large and diverse group of friends and acquaintances may be invited to multiple sites. Although the registration process is relatively simple for each site, having to maintain accounts on different sites that contain essentially the same information is, at least, an inconvenience. From a broader perspective, the multitude of potential sites divides the potential user base. Although the number of participants may be large for each site, it is not likely that one's extended, real social network will be fully represented by any one site. Additionally, pressure from one's friends to join new sites is likely to result in increased frustration and defection from the technology (Kahney, 2004).
Parallels may be drawn between the rise of SNS and instant messaging. The platform multiplicity problem described previously holds true for IM since multiple IM clients are available, each with a different user interface and access regime (Nardi, 2000, p. 2). Not long after IM took hold as a popular communications tool, the number of competing services began to decrease as different networks merged. Similar to these trends in IM, there is already some indication that SNS sites will merge with established Internet companies (Menn, 2003), either by using the experience of existing SNS sites to build their own applications, or simply by merging with existing services. Additionally, IM applications were introduced that bridged multiple IM networks which further eroded proprietary boundaries. What has not yet materialized are services that bridge multiple SNS sites or, alternatively, standard protocols for SNS networking, both of which have occurred with IM (Huang & Yen, 2003, p. 65; IETF, 2004).
Beyond the consideration of choice is a more fundamental problem with the lack of portability between sites. Without open standards for SNS applications, each site maintains redundant data on behalf of each user when such data should ideally be maintained in a more centralized manner (Pollard, 2004). In addition to the replication of user data, there is a redundancy in content data as well. Most of the major SNS sites each have groups, events listings, and some form of classifieds. Having unique content within each site takes advantage of an implicit reputation network wherein a user of a site expects a certain level of trust in the quality of content presented within that site – that the content is not fraudulent or of low interest and that the content can be traced directly back to a member of the site who is, ultimately, linked in some way to the user. Although the quality of the content may increase as a result of this separation from the public Web, the content would likely have more value if it were aggregated with other such content on other SNS sites, thus increasing the range and depth of available resources (Wellman, 1996, p. 5).
Looking beyond content to functionality, many of the tools offered on the existing sites duplicate the effort required by the user to maintain relationships in multiple communication venues. Many SNS sites have internal messaging and contact management systems that are used to communicate within the site's network. It is very likely that most of the users of these sites already use such tools on the client side for managing e-mail and contacts, which presents the user with a common personal information management problem: synchronization. With some modifications, the information handled by these features could be integrated with tools that the user is already using and familiar with. For instance, instead of relying on the internal messaging client within Friendster (or similar sites), an anonymous remailer service that sends messages the user's existing e-mail client could be used to serve the same anonymity function without the redundancy. Additionally, the site's internal messaging functions could be retained as a service for users without a fixed e-mail client. The security and trust concerns surrounding the open standards needed to make such improvements are not insignificant, but much research has been done in these areas (Langley, 2001; Resnick, 2000; Waldman, et al., 2001).
The intention that a user has for the SNS system which s/he takes part is important for understanding user behaviors. How a member of a SNS site uses the networking features depends ultimately on the motivation that the user has for participating in the network. These motivations may be introverted, extroverted, or a combination of the two. For example, a user of a recreational SNS may join because his or her friends request it. In this case, the locus of control(to paraphrase Philip Zimbardo) for the user is within the existing real social network of which s/he is a part. Such behavior should be considered introverted with respect to the existing social network. Alternatively, someone may decide to join an SNS site to meet new people or, otherwise, to experiment with an altered or alternate identity. In this case the locus of control is centered on external desires and should be considered extroverted. Extroverted users may take the behavior to the extreme, “friending” people merely to increase the number of friends in their network in order to gain access to a larger percentage of the entire network (Boyd, 2004, p. 2). Naturally, a combination of these two behaviors is common, where an individual will participate in a hybrid online/offline social network and simultaneously explore new relationships with people outside of the user's existing network.
A user's expression of intent is an artificially externalized behavior that occurs because current SNS applications enforce referential relationships in a binary manner (Boyd, 2004, p. 2; see also Figures 3 & 4). Either you announce another user as a friend or not, which, rather than the system taking into account the variable nature of personal relationships, places the burden of relationship judgment upon the user. Such design omissions are understandable in light of the complexity of the situation and the concomitant difficulty in automating such behaviors. For example, suppose a user of such an SNS decides to approach the use of the system from an introverted standpoint, only allowing people that s/he knows well to join their personal network. What happens when this user meets someone briefly, then finds that the new acquaintance wishes to be added to his/her personal network? The user is then faced with the decision to insult the new acquaintance by declining, or to bring this person into the personal network without knowing the person well. Adding an unfamiliar acquaintance effectively dilutes the overall strength of the ties in the user's personal network and potentially normalizes the behavior of the user in the virtual presence of this new person. Additionally, what happens when a relationship within the personal network loses its value through distance or other relationship changes? Does the user risk the once vibrant relationship by deleting the diminished tie from the personal network? These examples show that the boundaries of social networks are dynamic (Wellman, 1996, p. 6), which creates a tension between system design and usability.

Figure 3: Binary relationship enforcement in Friendster.
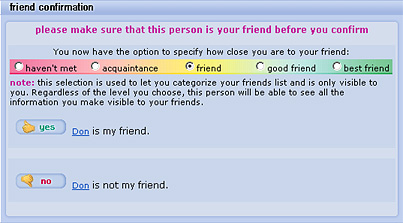
Figure 4: Semi-binary relationship enforcement in Orkut.
These quandaries come into sharp focus when SNS is applied to information activities that require a level of trust and emotional involvement, such as journaling and the revealing of private or sensitive information. For better or worse, many people would rather that acquaintances from work or family members were not privy to detailed information exchanged amongst friends. Indeed, many would also prefer to maintain boundaries between different groups of friends based on the user's relationship with the different groups, such as work related networks (e.g.: colleagues, managers, etc.) and leisure networks (e.g.: friends). Under the relationship regime of most SNS systems one would have to maintain separate accounts in order to accomplish this division (Boyd, 2002, p. 41).
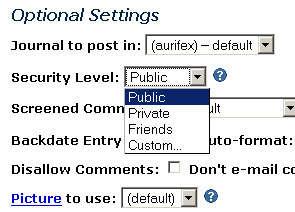
Figure 5: LiveJournal security settings.
One exception is LiveJournal, which allows the user to create custom security levels to determine which users or groups of users within the user's network may see entries in addition to whether entries can be seen by the public or only the user's network (LiveJournal, 2004, Support: FAQ, see also Figure 5). Another exception to this rule is the grading system provided by Orkut (Orkut, 2004; see also Figure 4), however, the grade given to a relation is for informational use by the grading user and has no effects on the information that may be viewed by the graded user. Relationship qualifying methods such as the one used by LiveJournal is a marked improvement over the binary means provided by other SNS sites, but requires additional effort for the user to establish and maintain.
Aside from creating separate accounts, a user that connects to different social groups would have to choose a median or lowest common denominator identity that would be acceptable to the majority of the network. Such a collapsing of the user's identity has the effect of restraining a person's ability to interact as s/he sees fit depending on who s/he is interacting with. Ideally, SNS applications should allow the user to modify their appearance and data to present consistent identities to different users and/or groups as determined by the user, just as it happens in physical interactions (Boyd, 2002, p. 43).
Potential Applications of SNS
The popularity of first generation of SNS applications has shown that a definite user interest exists and that the concept is valid from an information management perspective. Some of the problems with the current generation of SNS were discussed in the previous section. Among these problems is the lack of open standards for managing and sharing social networking data. Such open standards, if developed, could form a framework for managing communications and information exchange for all types of applications. This section makes some suggestions for future generations of SNS and its application to knowledge management, particularly in relationship management for business and personal applications and for content management.
Social networking sites such as Ryze were formed around the concept of building relationships between business professionals from the standpoint of providing opportunities for future employment and professional interchange. Such sites are popular because they model behaviors that are well established in real life: the “who-knows-who” of business. Within the boundaries of a company, social networks are also prevalent and could stand to benefit from SNS applications. SNS sites provide a model for ways which an organization can represent its employees as members of different workgroups, identify them as having specific areas of interest or competencies, and provide an overall knowledge management framework. Imagine Friendster or a similar site as an organizational Intranet: relations would be organized by formal workgroups instead of acquaintances, aggregated information would take the form of work-related information and experiences instead of personal anecdotes, and organizational resources could be exchanged instead of goods for sale. Techniques are already available for mining knowledge from communications (Kaihla, 2004, p.54), all that is remains to be done is to integrate these methods with a social networking interface.
In addition to business networking, SNS has great promise is in augmenting customer relationships. By leveraging a social network model for customer relationship management (CRM), prospects and customers can be seen as a node in a network instead of row in a database. This allows for a more holistic view of the communications touch-points that a company has with the customer, including sales, customer relations, and support. A white paper released by the Aberdeen Group (2004) describes a methodology for how SNS applications may assist organizations with CRM. The differences between SNS applications, such as Friendster, and the needs of a business looking to maintain customer relationships are described. In particular, people tend to join recreational SNS sites of their own volition and, usage intentions aside, approach new relationships within the system with similar intent as other users. In a customer relationship, the burden of establishing and maintaining the relationship is on the seller. Furthermore, sales associates in a business may be unwilling to share customer data with others in the organization for fear of losing the control that having the information brings (Aberdeen Group, 2004, p. 4). The paper presents an existing software application by Interface Software, InterAction, that applies a SNS methodology to sales relationship management (Aberdeen Group, 2004, p. 7). Additionally, extending this methodology with open social networking protocols completes the view that the organization has of potential customers. By allowing the prospect to control elements of his or her personal information, value is added to the relationship instead of allowing such information to become useless over time in private databases.
The benefits of social networking protocols to business communication are readily apparent since roles and relationships within and between workgroups are often well defined. The relationships we maintain in personal communications reflects often intangible decisions and impressions, which change over time and are difficult to model in a software system. Current SNS applications recognize this and leaves the semantics of the relationship up to the user to define and remember. If SNS is to mature beyond its current state, however, one may anticipate the need to make an attempt to simulate these judgments through some general means to assist one in deciding who to contact and under what circumstances, particularly in situations where physical contact is less frequent. In a situation that is somewhat analogous to the CRM example, one's personal contacts can be viewed as a node in a network, rather than simply an entry in an address book. For example, rather than addressing messages to individuals in an ad hoc manner, or by having to maintain and use pre-defined, relatively static, contact lists, messages could be sent to personal networks of interest. Sending information through interest networks, which are dynamically updated through social networking protocols and qualified by established reputation metrics, could both simplify messaging and add value to the underlying networks. Recommender systems and collaborative filtering (Kautz, et al., 1997) are examples of such interest-based applications for which open SNS protocols could build upon.
As a second example, relationships in business, whether contacts made for sales or for developing business opportunities, requires frequent attention in order to keep the relationship active. Integrating a SNS application with data mining of online communications platforms, such as e-mail and instant messaging, could allow the hybrid application to grade the relationships against contacts in the user's personal network by frequency of specific types of communication. People in the network who are contacted frequently would appear differently than those who have not, drawing attention to those relationships that are relatively neglected and may need attention. Alternatively, relationships could degrade over time if they are not renewed through new communication, bringing the same distinction to light. Similar applications could be used for maintaining personal connections as well. In this way, value is added to SNS by keeping a record of past transactions in a way similar to those of reputation systems (Resnick, et al., 2000, p. 45). Due to the variance of intent in communication, an absolutely positive valuation of messages or a one-to-one correlation between messages and positive communication is not desirable, but the concept is nonetheless worth exploring.
Finally, as previously mentioned, the current generation of SNS partitions content, whether individual data, forum postings, or other information, across multiple sites. To unify this content, standards must be developed for sharing content among different networks and establishing the trust and reputation systems necessary to ensure the content is valid, let alone desired (Pollard, 2004). Such systems sound on its face to be like those proposed for the agent-driven Semantic Web by Tim Berners-Lee (Berners-Lee, 2001). One of the major hindrances to implementing the Semantic Web is the massive effort required to generate and maintain descriptive elements of content and in defining trust relationships within a multi-faceted, opinionated environment. Perhaps future generations of SNS could provide the information for the basic content and reputation relationship platform of Semantic Web protocols?
Conclusion
The profusion of SNS sites and applications that have appeared in the past few years demonstrates a palpable interest in social networking applications by virtue of user demand. Social networks have been augmented by technology for some time, but now sufficient numbers of people have access to online resources such that the need for the technology to serve the social needs of its users is clear. The first generation of SNS applications has done much to justify the need for such services, as well as identified what must be improved in order to make the technology more useful. A unification of effort amongst the competing SNS applications is needed, as is a movement towards support for open protocols for access to its services and information. With further attention given to integration with existing technologies, SNS could greatly improve personal and organizational knowledge management.
References
Aberdeen Group (2004). Relationship capital management: Going beyond social networking to sell in relationship-based organizations: An executive white paper. Retrieved on 2 April, 2004, from http://www.interfacesoftware.com/aberdeen.
Berners-Lee, Tim, Hendler, James & Lassila, Ora (2001, May 17). The Semantic Web. Scientific American, 284(5), 34-44.
Boyd, Danah (2002). Faceted identity: Managing representation in a digital world. Masters thesis, Massachusetts Institute of Technology. Retrieved on 29 March, 2004, from http://smg.media.mit.edu/people/danah/thesis.
Boyd, Danah (2004). Friendster and publicly articulated social networks. Conference on Human Factors and Computing Systems (CHI 2004). Vienna: ACM, April 24-29, 2004.
Friendster (2004). Retrieved on 5 April, 2004, from http://www.friendster.com.
Hayes, Brian (2000). Graph theory in practice: Part I. American Scientist, 88(1). 9-13.
Huang, Albert & Yen, David (2003). Usefulness of instant messaging among young users: Social vs. work perspective. Human Systems Management, 22. 63–72.
Internet Archive (2004). SixDegrees.com: About the company. Retrieved on 4 April, 2004, from http://web.archive.org/web/19980416103302/sixdegrees.com/About/Company.cfm?PF=166181270631.
Internet Engineering Task Force (IETF) (2004). Instant messaging and presence protocol (impp). Retrieved on 23 April, 2004 from http://www.ietf.org/html.charters/impp-charter.html.
Kahney, Leander (2004, January 28). Social nets not making friends. Wired news. Retrieved on 3 April, 2004, from http://www.wired.com/news/culture/0,1284,62070,00.html.
Kaihla, Paul (2004, February 1). The matchmaker in the machine. Business 2.0, 52-55.
Kautz, Henry, Selman, Bart & Shah, Mehul (1997). Referral Web: Combining social networks and collaborative filtering. Communications of the ACM, 40(3). 63-65.
Kling, Rob (1996, July 1). Social relationships in electronic forums: Hangouts, salons, workplaces and communities. Computer-Mediated Communication Magazine, 3(7). Retrieved on 5 April, 2004, from http://www.december.com/cmc/mag/1996/jul/kling.html.
Langley, Adam (2001). Mixmaster remailers. In Andy Oram (Editor), Peer-to-peer: Harnessing the benefits of a disruptive technology (pp. 89-93). Sebastopol, CA: O'Reilly & Associates.
Lasen, Amparo (2002). The social shaping of fixed and mobile networks: A historical comparison. University of Surrey. Retrieved on 7 April, 2004, from http://www.surrey.ac.uk/dwrc/papers/HistComp.pdf.
Liu, Bob (2000, December 11). YouthStream Media to close subsidiaries. InternetNews.com. Retrieved on 7 April, 2004, from http://www.atnewyork.com/news/article.php/531761.
LiveJournal (2004). Retrieved from http://www.livejournal.com.
Menn, Joseph (2003, December 29). The personal links of three social-networking sites. Los Angeles Times. Retrieved on 2 April, 2004, from http://www.latimes.com/business/la-fi-friendster29dec29,1,4441636.story.
Meskill, Judith (2004, January 31). SNS picking and parsing. Message posted to The social software weblog, retrieved on 3 April, 2004, from http://socialsoftware.weblogsinc.com/entry/2127913924623224.
Mnookin, Jennifer L. (1996). Virtual(ly) law: The emergence of law in LamdaMOO. In Edward Barrett (Series Ed.) & Peter Ludlow (Vol. Ed.), Digital communication: Crypto anarchy, cyberstates, and pirate utopias (pp. 245-302). Cambridge, Massachusetts: The MIT Press.
Nardi, Bonnie, Whittaker, Steve & Bradner, Eric (2000). Interaction and outeraction: Instant messaging in action. Proceedings of CSCW 2000. Philadelphia, PA: ACM Press.
Orkut (2004). Retrieved on 5 April, 2004, from http://www.orkut.com.
Pollard, Dave (2004, February 5). What's wrong with first-generation social software. Message posted to the How to save the world weblog, retrieved on 3 April, 2004, from http://blogs.salon.com/0002007/2004/02/05.html.
Poster, Mark (2001). Postmodern virtualities. In Saul Ostrow (Series Ed.), Critical voices in art, theory and culture: The information subject (pp. 71-94). Amsterdam: G + B Arts International.
Reid, Elizabeth M. (1996). Communication and community on Internet relay chat: Constructing communities. In Edward Barrett (Series Ed.) & Peter Ludlow (Vol. Ed.), High noon on the electronic frontier: Conceptual issues in cyberspace (pp. 397-411). Cambridge, Massachusetts: The MIT Press.
Resnick, Paul, Zeckhauser, Richard, Friedman, Eric & Kuwabara, Ko (2000). Reputation systems. Communications of the ACM, 43(12), 45-49.
Rheingold, Howard (2002). Smart mobs: The next social revolution. Cambridge, MA: Basic Books.
Ryze (2004). Retrieved on 5 April, 2004, from http://www.ryze.com.
Smith, Marc (1992). Voices from the WELL: The logic of the virtual commons. Unpublished manuscript. Retrieved on 23 April, 2004, from http://research.microsoft.com/~masmith/Voices%20from%20the%20Well.doc.
Tribe.net (2004). Retrieved on 5 April, 2004, from http://www.tribe.net.
Waldman, Marc, Cranor, Lorrie F. & Rubin, Avi (2001). Trust. In Andy Oram (Editor), Peer-to-peer: Harnessing the benefits of a disruptive technology (pp. 242-270). Sebastopol, CA: O'Reilly & Associates.
Wellman, Barry (1996). For a social network analysis of computer networks: A sociological perspective on collaborative work and virtual community. Proceedings of SIGCPR/SIGMIS. Denver, CO: ACM Press.
Wellman, Barry, Salaff, Janet, Dimitrova, Dimitrina, Garton, Laura, Gulia, Milena & Haythornthwaite, Caroline (1996). Computer networks as social networks: Collaborative work, telework, and virtual community. Annual Review of Sociology, 22. 213-239.
| Attachment | Size |
|---|---|
| kiehne(2004)-sns.pdf | 276.41 KB |

